Total Fitness Exposes 500k Images of Members & Staff

Cybersecurity researcher Jeremiah Fowler discovered a non-password-protected database containing 474,651 images belonging to Total Fitness, a health club chain with 15 locations across North England and Wales. The database, which was 47.7 GB in size, included personal screenshots, profile pictures of members and their children, and facial images of gym employees. Some images contained highly sensitive information […]
Threat Actor Claiming of Israel’s Government API Database

A threat actor has claimed responsibility for breaching Israel’s government API database. The announcement was made via a post on social media X by the darkwebinformer. Details of the Breach According to the post, the threat actor claims to have accessed a vast array of data, including personal information of Israeli citizens, government communications, and […]
VLC Media Player Vulnerabilities Allow Remote Code Execution

VideoLAN, the organization behind the popular VLC Media Player, has disclosed multiple critical vulnerabilities that could allow attackers to execute arbitrary code remotely. These vulnerabilities affect both the desktop and iOS versions of the software. The security advisories, identified as SB-VLC3021 and SB-VLC-iOS359, outline several flaws malicious actors could exploit. SB-VLC3021: Desktop Version Vulnerabilities The vulnerability, which involves […]
Fortinet to Acquire AI-Powered Cloud Security Platform Lacework

Fortinet, a global leader in broad, integrated, and automated cybersecurity solutions, has announced its acquisition of Lacework, an AI-powered cloud-native application protection platform (CNAPP). This strategic move aims to enhance Fortinet’s already comprehensive cybersecurity platform by integrating Lacework’s advanced cloud security capabilities. The acquisition aligns with Fortinet’s growth strategy, which focuses on expanding its AI […]
Safari, Microsoft Edge, & DuckDuckGo Spoofing Flaws Impacting Millions of Users

RedSecLabs security researchers Rafay Baloch and Muhammad Samaak have uncovered address bar spoofing vulnerabilities in widely used mobile browsers such as Safari, Microsoft Edge, and DuckDuckGo. These vulnerabilities have a significant impact, affecting millions of users worldwide. The Severity of Address Bar Spoofing Google has highlighted the severity of address bar spoofing within their Google Vulnerability Reward […]
Chrome Introduced Shared Memory Versioning to Enhance Browser Performance

Google Chrome recently implemented Shared Memory Versioning, improving its speed through more effective cookie handling. This upgrade improves Chrome and other Chromium-powered browsers like Microsoft Edge and Vivaldi. Resource contention arises as more people rely on the Internet to do their daily tasks, placing increased demands on browsers to run several programs simultaneously. The multi-process Chrome browser […]
Hackers Employ JavaScript Framework To Trick Users Copy, Paste And Command Execution

Hackers use JavaScript frameworks since they offer a wide range of functionalities and tools that could be used to bypass detection, hide code, and carry out harmful acts. In addition, they take advantage of the people’s trust in such popular frameworks by developers as well as companies, making it simpler for them to evade security […]
Hackers Actively Exploiting Checkpoint 0-Day Flaw

Cybersecurity experts have identified a critical zero-day vulnerability in Checkpoint’s security software that hackers are actively exploiting. The flaw assigned to the identifier CVE-2024-24919 poses a significant threat to organizations relying on Checkpoint’s solutions for their cybersecurity needs. Details of the Vulnerability – CVE-2024-24919 The vulnerability, CVE-2024-24919, affects multiple versions of Checkpoint’s security software. It allows attackers […]
Microsoft Observed Huge-Surge In Attacks Targeting Internet-Exposed OT Devices In WWS
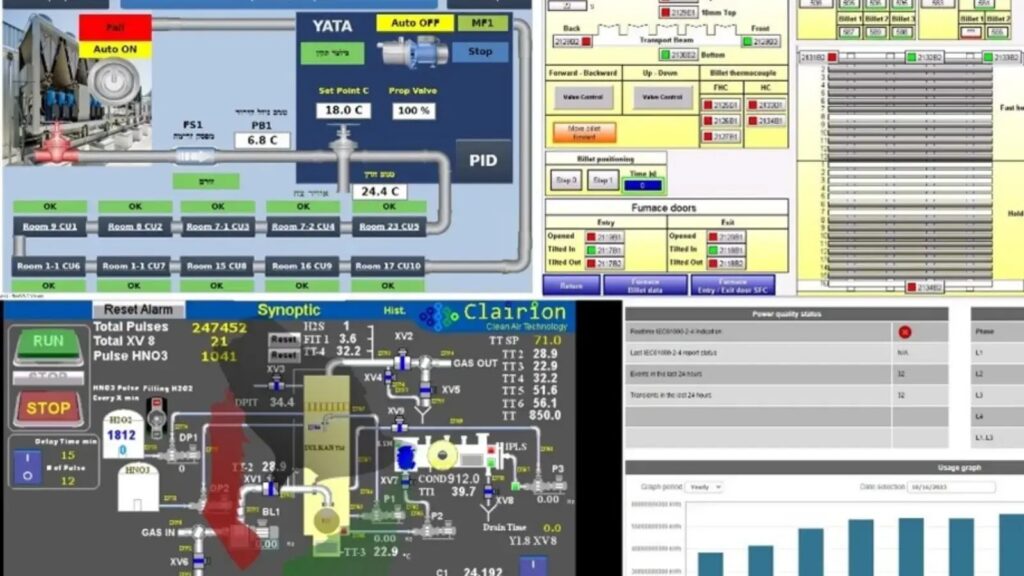
Microsoft has reported a significant increase in cyberattacks targeting internet-exposed, poorly secured operational technology (OT) devices. These attacks have particularly focused on the United States’ water and wastewater systems (WWS). Various nation-backed actors, including the IRGC-affiliated “CyberAv3ngers” and pro-Russian hacktivists, have been implicated in these attacks. Vulnerability of OT Systems OT systems control critical real-world […]
Indian Stock Exchange BSE Starts Encrypting Messages to Traders

The Bombay Stock Exchange (BSE) has begun encrypting messages sent to traders, becoming the first exchange in the world to implement such a system. The move aims to enhance security and protect sensitive information in the face of growing cyber threats. The BSE and the National Stock Exchange (NSE) have been working on measures to […]
