[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Cybersecurity firm Rapid7 has identified that popular Windows tools Notezilla, RecentX, and Copywhiz have been weaponized to deliver malware. These tools, developed by Conceptworld, an India-based company, are widely…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] A new vulnerability has been discovered in Ariane Allegro Scenario Player in a Kiosk mode that could allow threat actors to bypass the Kiosk mode and access the underlying…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Hackers use JavaScript frameworks since they offer a wide range of functionalities and tools that could be used to bypass detection, hide code, and carry out harmful acts. In…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] VideoLAN, the organization behind the popular VLC Media Player, has disclosed multiple critical vulnerabilities that could allow attackers to execute arbitrary code remotely. These vulnerabilities affect both the desktop…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Fortinet, a global leader in broad, integrated, and automated cybersecurity solutions, has announced its acquisition of Lacework, an AI-powered cloud-native application protection platform (CNAPP). This strategic move aims to…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] RedSecLabs security researchers Rafay Baloch and Muhammad Samaak have uncovered address bar spoofing vulnerabilities in widely used mobile browsers such as Safari, Microsoft Edge, and DuckDuckGo. These vulnerabilities have a significant…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Google Chrome recently implemented Shared Memory Versioning, improving its speed through more effective cookie handling. This upgrade improves Chrome and other Chromium-powered browsers like Microsoft Edge and Vivaldi. Resource contention arises…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] A threat actor has claimed responsibility for breaching Israel’s government API database. The announcement was made via a post on social media X by the darkwebinformer. Details of the…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Cybersecurity researcher Jeremiah Fowler discovered a non-password-protected database containing 474,651 images belonging to Total Fitness, a health club chain with 15 locations across North England and Wales. The database, which was…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Microsoft has announced a new way to spot potentially hacked machines in your organization. Analysts may now easily identify, examine, and search for suspicious interactive processes running on “hidden…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Hackers often abuse weaponized Word docs, as they can contain macros that contain or exploit flaws inside those Word files to run destructive code upon being opened by the…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] WordPress has released an urgent security update, version 6.5.5, addressing critical vulnerabilities that could potentially compromise the security of millions of websites. This minor release, which also includes three bug fixes…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] The Health Sector Cybersecurity Coordination Center (HC3) has issued a critical alert regarding a new ransomware strain, Qilin, which is targeting healthcare organizations worldwide. This revelation underscores the escalating…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] The Cybersecurity and Infrastructure Security Agency’s (CISA) Chemical Security Assessment Tool (CSAT) was the target of a cybersecurity intrusion by a malicious actor from January 23-26-2024. The breach, which has raised…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] ESET, a leading cybersecurity company, recently addressed a local privilege escalation vulnerability in its Windows security products. The Zero Day Initiative (ZDI) reported the vulnerability to ESET. It could have allowed…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Life360, a company known for its family safety services, recently fell victim to a criminal extortion attempt. The company received emails from an unknown actor claiming to possess Tile…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Researchers analyzed real-world passwords leaked on the dark web instead of artificial ones used in labs, as their findings showed that a worrying 59% of these passwords could be…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”]A newly discovered security vulnerability allows attackers to impersonate Microsoft corporate email accounts, significantly increasing the risk of phishing attacks. Security researcher Vsevolod Kokorin, also known as Slonser, found this…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] “Encrypted DNS Implementation Guidance,” a detailed document from the Cybersecurity and Infrastructure Security Agency (CISA), tells government agencies how to improve their cybersecurity by using encrypted Domain Name System…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Earth Hundun, a notable Asia-Pacific malware organization, uses Waterbear and Deuterbear. We first encountered Deuterbear in Earth Hundun’s arsenal in October 2022, signaling its implementation. This report describes the ultimate Remote…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Cybersecurity experts have identified a new malware, dubbed WaveStealer, that is being actively distributed through popular messaging platforms Telegram and Discord. This sophisticated malware masquerading as video game installers poses a…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] According to the Federal Communications Commission (FCC), the Royal Tiger Group and its employees are a Consumer Communications Information Services Threat (C-CIST). This is a crucial step for the…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] A major mistake in setup caused Google Cloud and UniSuper to delete the financial service provider’s private cloud account. This event has caused a lot of worry about the security and…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Google has released an urgent update for its popular Chrome web browser. The update fixes a critical zero-day vulnerability that malicious attackers are actively exploiting. The vulnerability is considered…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] The Federal Bureau of Investigation (FBI) has warned about a sophisticated phishing and smishing (SMS phishing) campaign orchestrated by a cybercriminal group known as STORM-0539, or Atlas Lion. This…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] The City of Wichita, Kansas, experienced a disruption when it fell victim to a ransomware attack. This cyber assault encrypted data across various city systems, prompting officials to shut down the…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Cybersecurity experts have identified a critical zero-day vulnerability in Checkpoint’s security software that hackers are actively exploiting. The flaw assigned to the identifier CVE-2024-24919 poses a significant threat to…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Microsoft has reported a significant increase in cyberattacks targeting internet-exposed, poorly secured operational technology (OT) devices. These attacks have particularly focused on the United States’ water and wastewater systems…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] The Bombay Stock Exchange (BSE) has begun encrypting messages sent to traders, becoming the first exchange in the world to implement such a system. The move aims to enhance…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] A new piece of malware called CasperSecurity Stealer is a major threat to Windows computers. This complex malware is made to steal Remote Desktop Protocol (RDP) credentials, which is very dangerous…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] The Insikt Group at Recorded Future has found a sophisticated cybercrime operation run by Russian-speaking threat actors from the Commonwealth of Independent States (CIS). This group of hackers has…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Kapeka, also known as KnuckleTouch, is a sophisticated backdoor malware that has been making waves in the cybersecurity world. Initially appearing in mid-2022, it wasn’t until 2024 that Kapeka was formally…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] A Russian citizen has been indicted for working as an “access broker” and selling unauthorized access to computer networks, including a victim company in New Jersey, U.S. Attorney Philip R. Sellinger,…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] The notorious data breach forum, Breachforums, has re-emerged after being confiscated by authorities in a surprising development. According to the recent tweet from Dark Web Informer, the news has…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Cybersecurity experts have identified a critical zero-day vulnerability in Pulse Connect Secure VPN, a widely used virtual private network solution. The vulnerability, which allows for remote code execution (RCE), has been…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Cybersecurity professionals at Sygnia have noted a notable change in the strategies used by ransomware groups that are aiming at virtualized environments, specifically VMware ESXi infrastructure, in relation to…
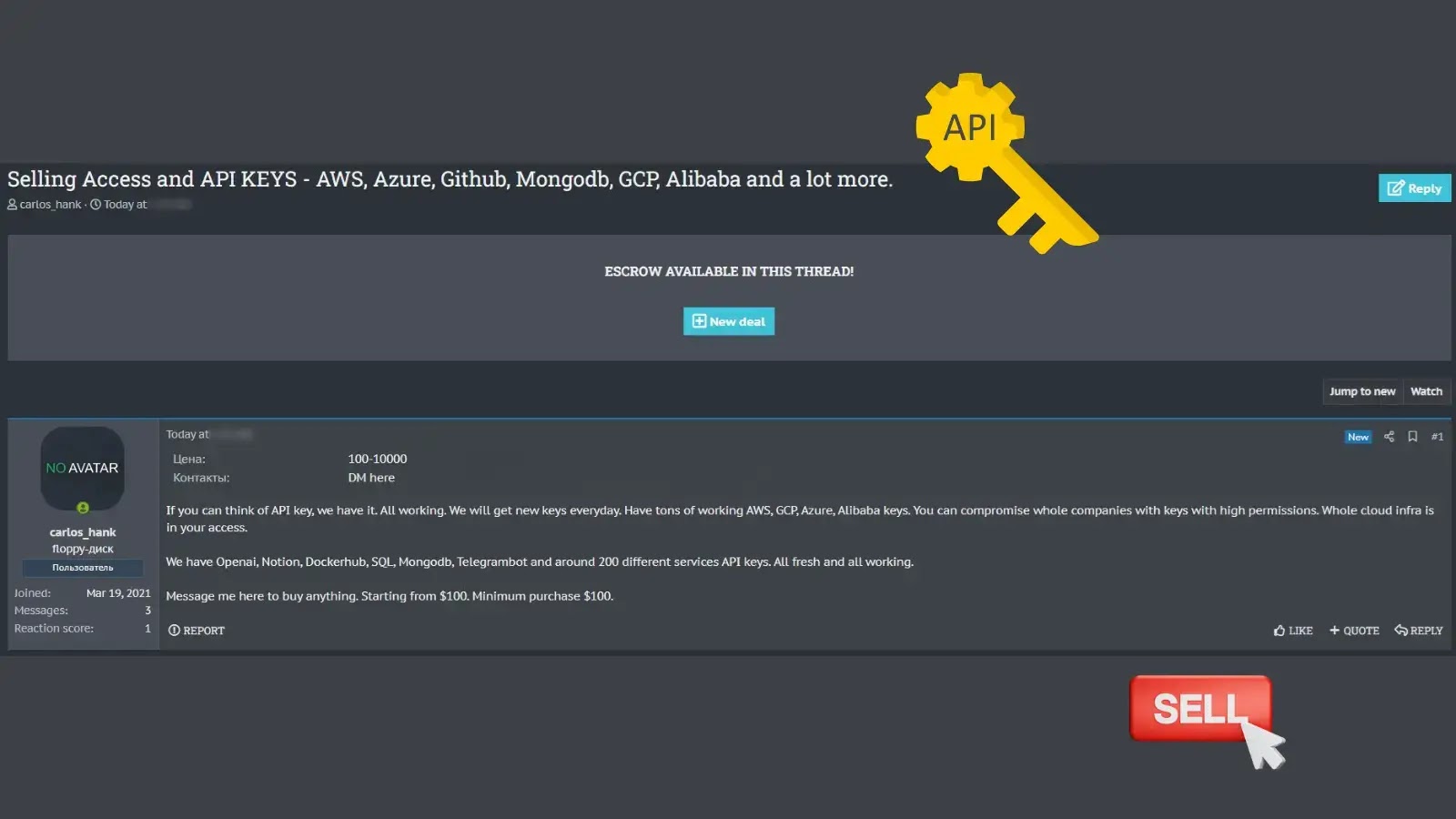
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] A threat actor has claimed to have gained unauthorized access to API keys for major cloud service providers, including Amazon Web Services (AWS), Microsoft Azure, MongoDB, and GitHub. The announcement was…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Rockwell Automation has sent an urgent message to all of its customers because of rising geopolitical issues and hostile cyber activity worldwide. The company is asking that any devices…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Introduction The demand for cybersecurity skills is on the rise in today’s hyper-connected and digitized world, where cyber dangers are constantly evolving. The demand for qualified individuals in the…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Introduction The phrase “zero-day vulnerability” sends chills down the spines of security professionals and everyday people alike in the constantly changing world of cybersecurity. One of the most serious…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Introduction: The way we communicate and engage with numerous devices has been revolutionized by Bluetooth technology. Bluetooth is now found in every aspect of our everyday lives, from smart…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] The Importance of Supply Chain Risk Management Introduction: Organizations are accountable for protecting their supply chains from cyber-attacks in addition to defending their internal networks in an increasingly connected…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Introduction: Security flaws and exposes put computer systems and software programs at serious risk in today’s fast-paced technological world. The Common Vulnerabilities and Exposures (CVE) system was developed to…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Introduction: Understanding the numerous flaws that could compromise the security of computer systems is essential in the field of cybersecurity. The stack-based buffer overflow is one such flaw that…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Introduction: It is crucial in the field of cybersecurity to quickly identify and fix flaws that could be used by malevolent parties to their advantage. The Common Desktop Environment…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Introduction: Security is crucial in the domain of operating systems for protecting sensitive data and guaranteeing the general integrity of the system. But occasionally, flaws appear that might leave…
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry’s standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a…
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry’s standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Introduction The global pandemic caused an unprecedented change in how we work, resulting in the development of the work-from-home (WFH) culture. While many industries experienced difficulties as a result…
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry’s standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] McAfee has introduced a significant upgrade to its AI-powered deepfake detection technology. This enhancement, developed in collaboration with Intel, aims to provide a robust defense against the escalating threat…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Operation PANDORA has successfully dismantled a network of 12 fraudulent call centers, dealing a significant blow to a sophisticated criminal enterprise that has stolen over €10 million from unsuspecting…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Cybersecurity communities are on high alert as threat actors have begun selling Remote Desktop Protocol (RDO) access on underground hacker forums. This alarming trend poses significant risks to individual…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] It has been found that almost one-fifth of the repositories on Docker Hub, a popular platform for developers to store and share containerized applications, have been exploited to spread…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Many generations might have passed on and many generations may come in future. But one thing that will remain common across an individual or group is the thought of…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Jareh Sebastian Dalke, 32, of Colorado Springs, was sentenced today to 262 months in prison for attempted espionage in connection with his efforts to transmit classified National Defense Information…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] ICICI Bank, one of India’s leading private banks, has confirmed the exposure of sensitive credit card information belonging to thousands of customers. The Mumbai-based bank acknowledged that a technical…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Google announced the release of Chrome 124, which fixes four vulnerabilities, including a critical security issue that allows attackers to execute arbitrary code. Over the next few days or weeks,…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] Google has announced that external participants without Google accounts can join client-side encrypted Google Meet calls. This move marks a substantial step in balancing user accessibility with robust security measures. Google…
[responsivevoice_button rate=”1″ pitch=”1.2″ volume=”0.8″ voice=”US English Female” buttontext=”Click Here to Listen”] A new type of malware dubbed “Wavestealer” has been identified. This malicious software reportedly steals sensitive information such as login credentials and credit card data from unsuspecting users. Wavestealer…