
Hackers use JavaScript frameworks since they offer a wide range of functionalities and tools that could be used to bypass detection, hide code, and carry out harmful acts.
In addition, they take advantage of the people’s trust in such popular frameworks by developers as well as companies, making it simpler for them to evade security controls.
Moreover, JavaScript, on its part, is cross-platform and open to multiplatform attacks.
Cybersecurity researchers at ReliaQuest identified that hackers employ JavaScript frameworks to trick users into copying, pasting, and executing commands.
Hackers Employ JavaScript Framework
In May 2024, ReliaQuest discovered another campaign by the ClearFake JavaScript framework that requires users to manually copy and execute harmful PowerShell code as opposed to the drive-by downloads, where it is just clicked.
This method intends to avoid security tools while the commands are run directly by a user, leading to multi-stage malware infection and installation of LummaC2 infostealer.
Although less likely to fool users successfully, it could bypass detections and controls if done right.
PowerShell restrictions must be reviewed in organizations, users should be educated, and mitigations must be implemented against this newly emerging threat.
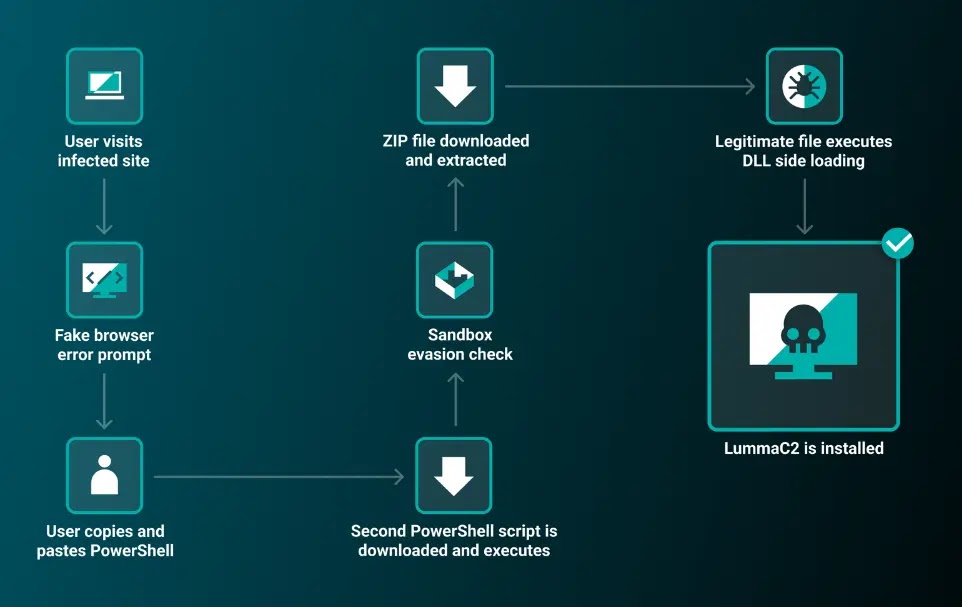
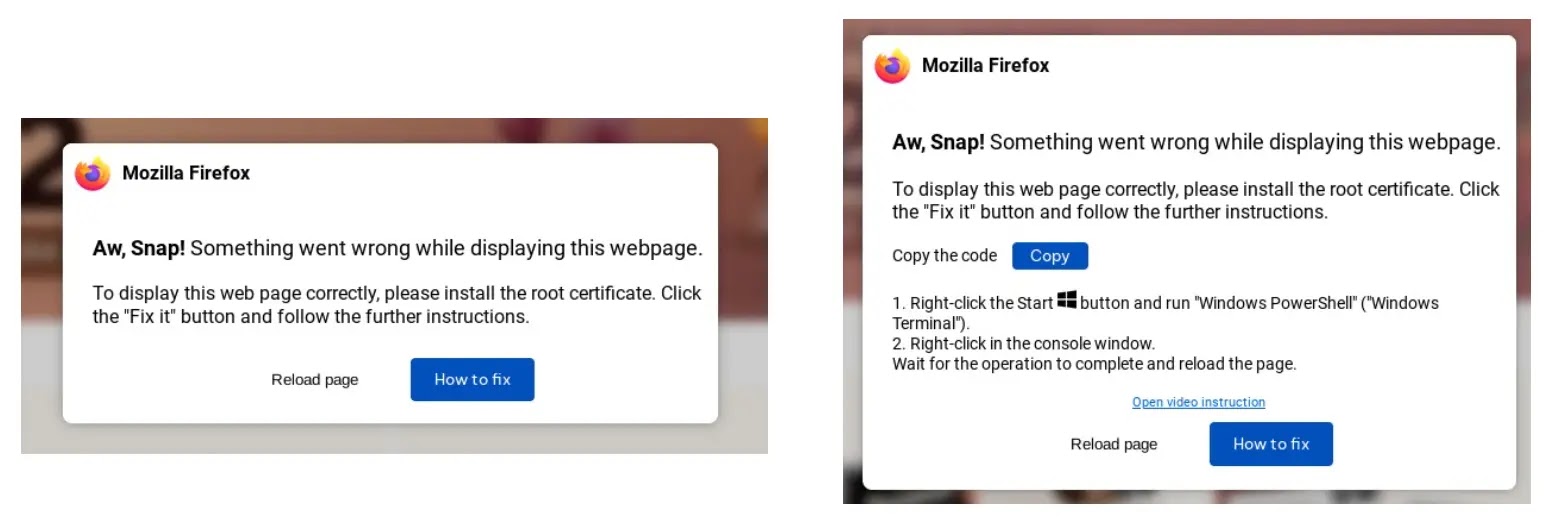
In a recent campaign, it broke into real websites to show fake browser errors, asking the user to run obscure PowerShell commands that would install a “root certificate.”
It evades detection by initiating the Explorer.exe without any parent process or command line.
When executed manually, the base64 encoded PowerShell code finally drops LummaC2 malware onto compromised machines.
Once the PowerShell execution has been obscured, the attacker domain makes a user agent check, and then another PowerShell script is downloaded.
In this manner, it checks CPU temperature for sandbox avoidance, and if it is null, it stops running the script. Otherwise, it will download a ZIP file containing an original MediaInfo.exe and a malware DLL.
Consequently, when MediaInfo.exe runs, it loads the LummaC2 malware payload through DLL sideloading.
Recommendations
Here below we have mentioned all the recommendations:-
- Deploy application control to restrict unauthorized PowerShell execution.
- Enhance user awareness on threats of executing untrusted code.
- Regularly patch websites and tools to prevent code injection vulnerabilities.
- Block access to suspicious newly registered domains like .xyz TLDs.
- Implement restrictive WDAC policies to constrain malicious PowerShell functions.
- Integrate endpoint security with AMSI for script command analysis.
- Enforce restrictive PowerShell execution policies.
IOCs
Hashes
- a467302da10ace0bf96963bcd6bdcd6a4e619e28cd477612988276dfee9f429e
- 4d417cff26e83e096f6c161a10d6a72774b8bbc8948bf5b6d3156e6f17adac5f
- 4a058f08157863034a6df89cddc13e81a561eb9ca0e955f4fe38f4ba7b4fa9f7
- 44a45c396516a3f2705eaf9751a06d346fcae1864f5521356349ce85e78fd386
Attacker-Controlled Domains
- baqebei1[.]online
- cdnforfiles[.]xyz
- d1x9q8w2e4[.]xyz
Attacker-Controlled IP Addresses
- 104[.]21[.]29[.]92
- 172[.]67[.]148[.]183
- 188[.]114[.]97[.]7
Infected Websites
- lambhuaexpress[.]in
- soundmine[.]me
- helena[.]pe
- rijas[.]com
- navigatingthisspace[.]com
- sportrealeyes[.]it
- areadeturismo[.]tur[.]ar
- th3sport24[.]com
- manchac[.]com
- tonitto[.]com
- aedjakodu24[.]ee
Source: https://bit.ly/3uS5LZ2
