Beware of Weaponized Notezilla, RecentX, & Copywhiz Windows Tools that Deliver Stealing Malware
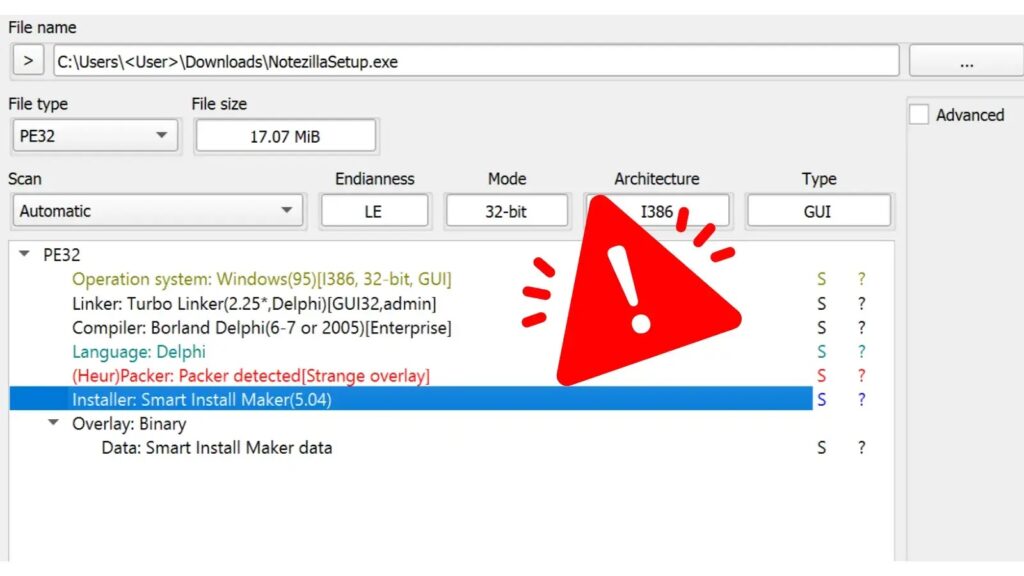
Cybersecurity firm Rapid7 has identified that popular Windows tools Notezilla, RecentX, and Copywhiz have been weaponized to deliver malware. These tools, developed by Conceptworld, an India-based company, are widely used for productivity enhancements. However, the installation packages available on the official Conceptworld website have been found to execute malware alongside legitimate software, posing significant risks to users. […]
WordPress Releases Urgent Security Update to Patch XSS and Path Traversal Flaws

WordPress has released an urgent security update, version 6.5.5, addressing critical vulnerabilities that could potentially compromise the security of millions of websites. This minor release, which also includes three bug fixes in the core, is highly recommended for immediate installation to ensure site security and stability. Key Security Fixes The WordPress 6.5.5 update addresses three significant security […]
HC3 Unveils Qilin Ransomware Attacking Global Healthcare Organizations

The Health Sector Cybersecurity Coordination Center (HC3) has issued a critical alert regarding a new ransomware strain, Qilin, which is targeting healthcare organizations worldwide. This revelation underscores the escalating cyber threats facing the healthcare sector, which is already grappling with the complexities of digital transformation and the ongoing COVID-19 pandemic. The Emergence of Qilin Ransomware Qilin ransomware, […]
CISA’s CSAT Tool Hacked, Systems Taken Offline

The Cybersecurity and Infrastructure Security Agency’s (CISA) Chemical Security Assessment Tool (CSAT) was the target of a cybersecurity intrusion by a malicious actor from January 23-26-2024. The breach, which has raised significant concerns within the cybersecurity community, potentially exposed sensitive information including Top-Screen surveys, Security Vulnerability Assessments, Site Security Plans, Personnel Surety Program (PSP) submissions, and CSAT […]
ESET Security Products for Windows Vulnerable to Privilege Escalation

ESET, a leading cybersecurity company, recently addressed a local privilege escalation vulnerability in its Windows security products. The Zero Day Initiative (ZDI) reported the vulnerability to ESET. It could have allowed attackers to misuse ESET’s file operations during a restore operation from quarantine, potentially leading to an Arbitrary File Creation Local Privilege Escalation. CVE-2024-2003 – Vulnerability Details […]
Life360 Breach: Hackers Accessed the Tile Customer Support Platform

Life360, a company known for its family safety services, recently fell victim to a criminal extortion attempt. The company received emails from an unknown actor claiming to possess Tile customer information. Upon receiving these emails, Life360 promptly investigated and detected unauthorized access to the Tile customer support platform. The compromised data includes names, addresses, email addresses, phone […]
Hackers Can Crack Down 59% Of Passwords Within A Hour

Researchers analyzed real-world passwords leaked on the dark web instead of artificial ones used in labs, as their findings showed that a worrying 59% of these passwords could be cracked within an hour using just a modern graphics card and some technical knowledge, highlighting the weakness of many real-world passwords and the effectiveness of brute-force […]
New Security Vulnerability Let Attackers Microsoft Corporate Email Accounts
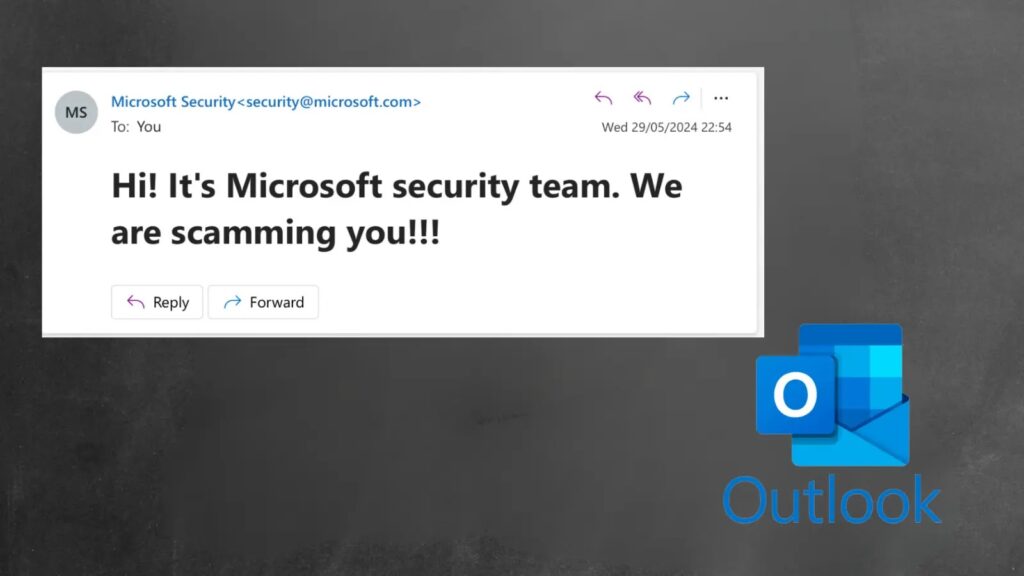
A newly discovered security vulnerability allows attackers to impersonate Microsoft corporate email accounts, significantly increasing the risk of phishing attacks. Security researcher Vsevolod Kokorin, also known as Slonser, found this bug, which Microsoft has not yet patched. Kokorin revealed the bug on X (formerly Twitter) after Microsoft dismissed his initial report, claiming they could not […]
Hackers Using Weaponized Word Documents In QR Code Phishing Attacks
Hackers often abuse weaponized Word docs, as they can contain macros that contain or exploit flaws inside those Word files to run destructive code upon being opened by the intended victims. It enables an attacker to employ this tool to deliver a payload to a target system or unauthorized access to a targeted system by […]
Microsoft Unveils Ways To Detect Compromised Devices In Your Organization

Microsoft has announced a new way to spot potentially hacked machines in your organization. Analysts may now easily identify, examine, and search for suspicious interactive processes running on “hidden desktops” using Defender for Endpoint’s “DesktopName” field. These days, remote desktop protocol (RDP) compromise usage has reached record highs, and ransomware operations are still expanding, making it even […]
