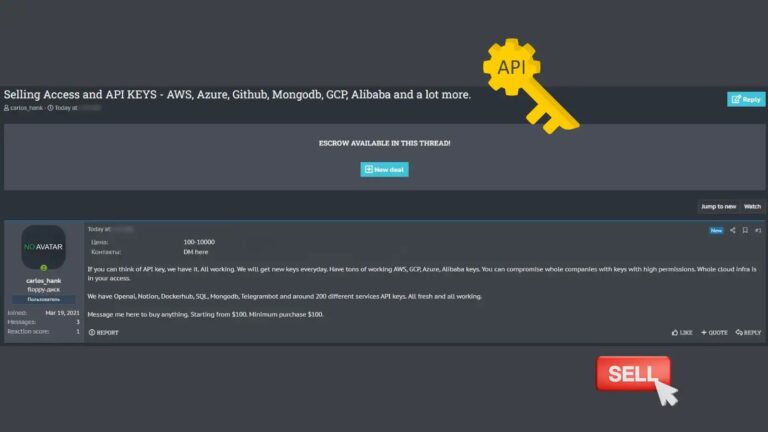
A threat actor has claimed to have gained unauthorized access to API keys for major cloud service providers, including Amazon Web Services (AWS), Microsoft Azure, MongoDB, and GitHub.
The announcement was made via a post on the social media platform X by the account DarkWebInformer.
The tweet has raised alarms within the cybersecurity community, prompting immediate investigations by the affected companies and security experts worldwide.
Potential Impact
Unauthorized access to API keys poses a severe risk as these keys can be used to access sensitive data, manipulate cloud resources, and potentially disrupt services.
API keys are essentially digital keys that allow applications to interact with cloud services, and if compromised, they can lead to data breaches and financial losses.
Security experts warn that the exposure of these keys could lead to:
- Unauthorized access to sensitive data stored in cloud databases.
- Manipulation or deletion of cloud resources.
- Potential for large-scale data breaches affecting millions of users.
Response from Affected Companies
In response to the claims, AWS, Azure, MongoDB, and GitHub representatives have issued statements assuring users that they are investigating the matter.
They have also advised users to rotate their API keys and implement additional security measures such as multi-factor authentication (MFA) and monitoring for unusual activity.
Similarly, Azure and MongoDB have recommended immediate key rotation and enhanced security protocols.
GitHub has also emphasized the importance of securing API keys and provided users with guidelines.
Here is a sample code snippet for rotating AWS API keys using the AWS Command Line Interface (CLI) to help users secure their accounts.
Users are encouraged to follow similar procedures for other cloud services and to stay vigilant against potential security threats.
As the investigation continues, organizations and individuals must proactively secure their cloud environments and protect their data from potential breaches.
Source: https://bit.ly/3uS5LZ2
