
RedSecLabs security researchers Rafay Baloch and Muhammad Samaak have uncovered address bar spoofing vulnerabilities in widely used mobile browsers such as Safari, Microsoft Edge, and DuckDuckGo.
These vulnerabilities have a significant impact, affecting millions of users worldwide.
The Severity of Address Bar Spoofing
Google has highlighted the severity of address bar spoofing within their Google Vulnerability Reward Program (VRP) guidelines.
According to Google, address bar spoofing poses a significant threat as it undermines modern browsers’ only reliable security indicator.
This makes it a critical issue that needs immediate attention.
Under RedSecLabs’ responsible disclosure policy, vendors were given a 60-day window to promptly address these vulnerabilities. However, vendors took longer than expected.
Following the report, the vulnerabilities were eventually fixed in Apple Safari and Microsoft Edge browsers.
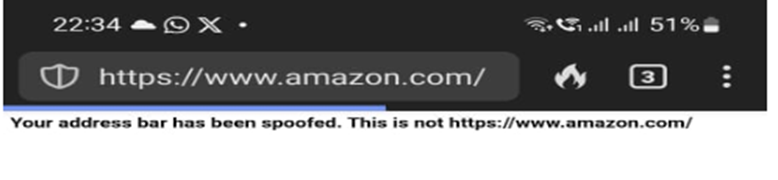
Imagine browsing the internet on your mobile device, thinking you’re on a safe website, only to realize that the address bar has deceived you. This deceptive tactic is known as Address Bar Spoofing.
Cybercriminals manipulate the URL of a malicious website to mimic legitimate ones like google.com, bing.com, facebook.com, or apple.com.
This makes it difficult to verify website authenticity and allows attackers to trick users into disclosing personal information or downloading malware easily.
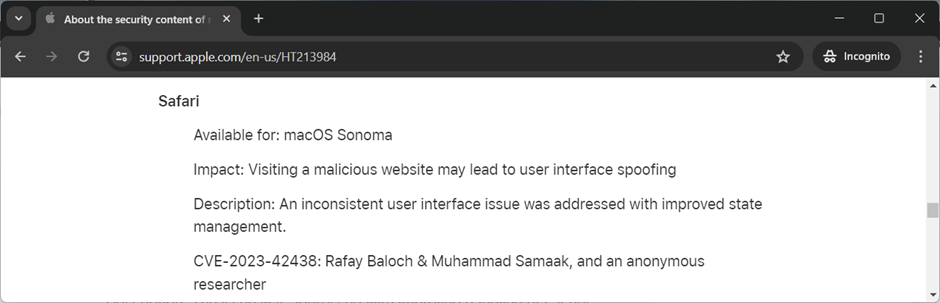
CVE-2023-42438 – Vulnerabilities in Safari & Edge
Safari
Apple Safari is one of the most widely used browsers, with an estimated 984 million users globally.
Additionally, Safari accounts for 24.71% of global mobile device browsers, a significant figure given Apple’s 28.83% smartphone market share.
Despite its popularity, Safari isn’t immune to vulnerabilities.
An address bar spoofing vulnerability was found in Safari version 9.5.
After Apple had reported the issue, the vulnerability was addressed, and CVE-2023-42438 was assigned.
Microsoft Edge
Like Safari, Microsoft Edge Browser for iOS was also vulnerable to an address bar spoofing attack.

The report was submitted to the Microsoft MSRC program.
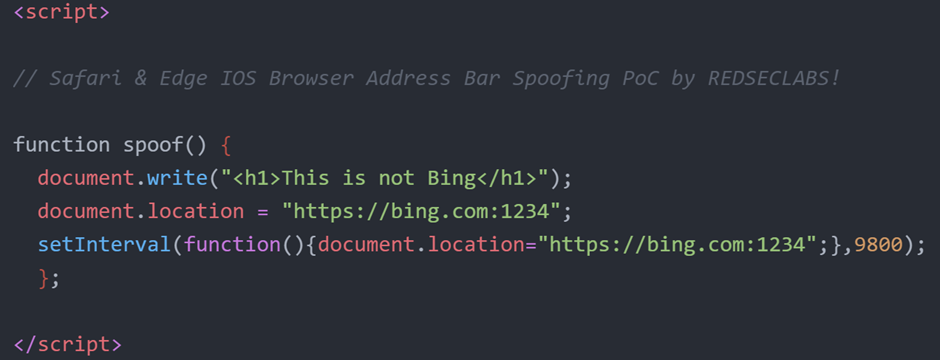
The exploit involves using the set interval function to reload the bing.com with no existing port “bing.com:8080” every 9.8 seconds.
This constant reloading can confuse users regarding the authenticity of the URL during redirection.
The privacy-focused browser DuckDuckGo, boasting over 5 million downloads, was also discovered vulnerable to an address bar spoofing attack.
The report was submitted via the HackerOne platform; however, the DuckDuckGo security team marked it as a duplicate.
Proof of Concept
The exploit involves using the set interval function to reload the bing.com with no existing port “bing.com:8080” every 9.8 seconds.
This constant reloading can confuse users regarding the authenticity of the URL during redirection.
The discovery of these address bar spoofing vulnerabilities in Safari, Microsoft Edge, and DuckDuckGo underscores the critical need for robust security measures in web browsers.
As millions of users rely on these browsers for their daily internet activities, ensuring their safety and security is paramount.
The timely intervention by RedSecLabs and the subsequent fixes by the vendors are commendable steps toward safeguarding user data and maintaining trust in digital platforms.
Source: https://bit.ly/3uS5LZ2
