
Researchers analyzed real-world passwords leaked on the dark web instead of artificial ones used in labs, as their findings showed that a worrying 59% of these passwords could be cracked within an hour using just a modern graphics card and some technical knowledge, highlighting the weakness of many real-world passwords and the effectiveness of brute-force attacks with GPUs.
Password cracking refers to retrieving the original password from its hashed form. Traditionally, passwords were stored in plain text, making them vulnerable to data breaches.
Modern systems address this by using hashing algorithms like SHA-1 to convert passwords into unique, fixed-length hash values. When a user logs in, their entered password is hashed and compared to the stored hash, and if they match, access is granted.
Crackers aim to decrypt the hash back to the original password, often using rainbow tables, which pre-compute hashes for common passwords. This allows them to access compromised accounts and potentially others where the same password was reused.
To enhance password security, password hashing with salt incorporates a random data string (salt) before applying a hashing function, which can be dynamically generated or static, creating unique password-salt combinations for each user.
Feeding this combination into the hashing algorithm creates a distinct hash, rendering pre-computed rainbow tables ineffective for attackers. Consequently, this method significantly increases the difficulty of cracking passwords.
Modern GPUs are significantly faster than CPUs for password cracking. For instance, an RTX 4090 paired with a hashcat can analyze 164 billion hashes per second for salted MD5 hashes, while an 8-character password using uppercase/lowercase letters and digits (36 characters each) has 2.8 trillion combinations.
A powerful CPU (6.7 GH/s) could crack this password in 7 minutes, while an RTX 4090 (164 GH/s) needs only 17 seconds.
Even without owning such GPUs, attackers can rent them for a few dollars per hour, enabling them to crack massive leaked password databases efficiently.
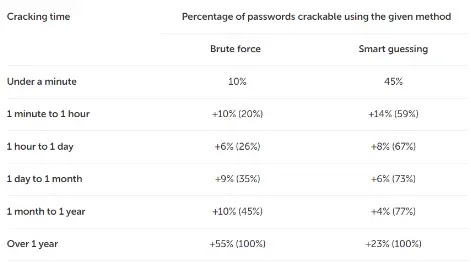
Researchers at Kaspersky analyzed real-world passwords and found that many are vulnerable to cracking.
Using a combination of brute-force and smart-guessing algorithms, they cracked 45% of passwords in under a minute and 59% within an hour.
Smart-guessing algorithms achieved this by prioritizing common character combinations. This emphasizes that cracking all passwords in a database takes roughly the same time as cracking one because each guess is checked against a database of hashed passwords.
Password cracking algorithms leverage human predictability to efficiently guess combinations, where people favor common phrases, dates, and patterns, making them vulnerable to dictionary attacks.
Even attempts at randomness are biased towards keyboard center keys, allowing algorithms to crack most passwords containing dictionary words or frequent symbol combinations within minutes or hours.
Basic substitutions like “pa$$word” or “@” for letters offer minimal protection. Similarly, including popular words or number sequences like “123456” significantly weakens passwords.
Source: https://bit.ly/3uS5LZ2
