
A new vulnerability has been discovered in Ariane Allegro Scenario Player in a Kiosk mode that could allow threat actors to bypass the Kiosk mode and access the underlying Windows Desktop.
The CVE for this vulnerability is yet to be assigned by the severity for the Kiosk Mode Bypass has been given as 6.3 (Medium).
However, this vulnerability was discovered in the Ariane Duo 6000 series, which runs the Ariane Allegro Scenario Player.
Researchers tried contacting Ariane Systems to report this vulnerability by any means.
Since they did not respond after 90 days, this vulnerability has been published.
Technical Analysis
According to the reports, Ariane Systems is a leading self-check-in and out solutions provider. Their kiosk mode systems were used in more than 3000 hotels and 500,000 rooms in more than 25 countries.
Nevertheless, these kiosk machines had a glaring weakness that allowed attackers to crash the machine.
The kiosk mode check-in and check-out allows users to enter their names on the system.
When the user enters a single quote (‘), the terminal gets stuck without any activities.
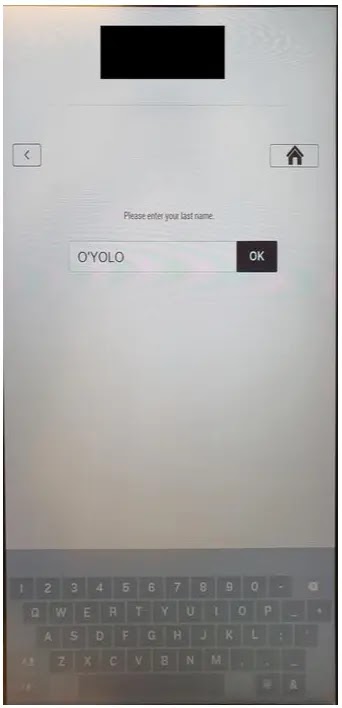
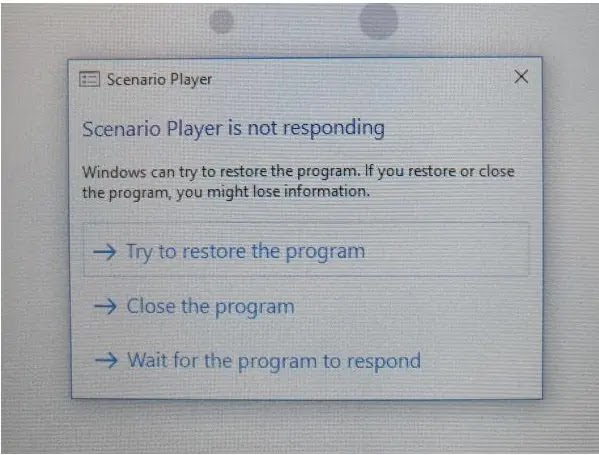
Upon touching the screen, the Windows Crash report dialogue box shows up asking for three options such as “Try to restore the program”, “Close the program”, “Wait for the Program to Respond”.
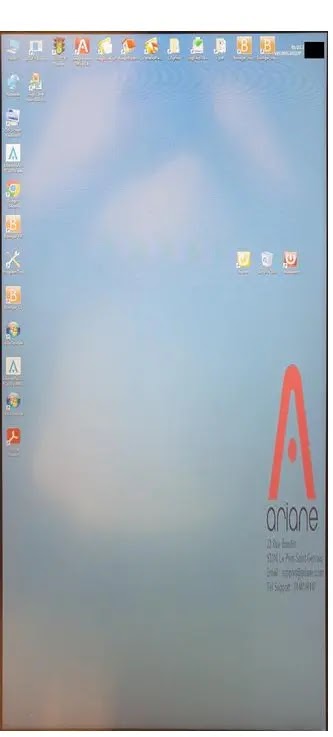
If users click on “Close the program,” the Allegro Scenario Player closes, and a Windows Desktop with many options is displayed.
On researching further, researchers discovered many options available for an attacker to exploit the system, such as accessing the data stored on the terminal, including PII, reservations, and invoices, injecting and executing malicious programs, or even getting room keys created for other rooms.
Room key access collection was possible due to the RFID transponders feature available on the Ariane systems, which allows the user to open the booked hotel room and also print an invoice.
Further, the Ariane system also initiates the payment process via a POS terminal, which is now accessible.
However, the only prerequisite for an attacker to exploit this vulnerability is physical access to the check-in terminal, which is enabled for self-service, which is available in most hotels during specific times.
This vulnerability exists, and there are no patches to fix it yet. But as a workaround, users can isolate the check-in terminals to prevent these kinds of bypass activities.
Source: https://bit.ly/3uS5LZ2
